Ok, Ok, I'm Turning uPnP off.
I recently wrote a blog post concerning my discovery that my NAS had decided to expose itself all over the internet. If you haven’t seen that, it’s probably worth reading first. That post took off in a way I wasn’t quite expecting, and of course I didn’t quite dot my Is and cross my T’s as well as I should have, leading to a fair bit of misunderstanding in the HN post that initially kicked all this off. Hopefully I can address some of this here. I certainly didn’t think this would get a CVE!
Firstly, I’ll recount my contact with Terramaster. On Feb 21st 2021 I contacted Terramaster informing them of the issue. I contacted them again soon after again letting them know that changing the web server port does not help. I then contacted them a third time letting them know that this could be fixed fairly easily with a simple change to /etc/upnp.json as I mentioned in my previous post.
Terramaster replied on Feb 22nd saying they’d get someone to look into it, but also stated that this was intentional behavior:
Hello Kevin,
Thank you for contacting TerraMaster.
As for the mentioned security issue, it has been transferred to the R&D department, they will test here and fix it if it’s confirmed.
For port 8181 and 5443, it’s opened by default for it’s the default port of TOS webpage access.
I replied:
Hi,
Thanks for the confirmation that somebody will look into this.
Opening these ports via UPNP is not necessary for local access, and in fact makes the port accessible worldwide, externally.
I can also access my NAS via http://some-public-ip:8181 - on the public internet.
I hope that makes things clearer. Please me me know if you decide to change this behavior and if you do plan to fix this, please let me know what kind of timeline you’re working to. I’d like to publish a blog post about this (specifically around the danger of UPNP) once you’re happy everything is secure.
I then made the blog post 6 weeks later, hoping it might motivate them into fixing it. It sparked a lot of interesting discussion on Hacker News and Reddit /r/datahoarder. It blew up way bigger than I expected, and is by far the best performing blog post I’ve written. Pretty sad considering I threw it together in under an hour and didn’t even spell check it!
The issue specifically is that while the NAS claims its web interface is only locally accessible, it is actually accessible from anywhere in the world to anyone who knows the public IP of the network it is sitting on. This is because most consumer grade routers like the one I use have a feature called uPnP, which allows applications on your internal network to punch open ports that they need to operate. This feature is supposed to be useful for things like VOIP applications and gaming. The NAS for some reason decided to punch itself some ports open so that it could be internet accessible.
An interesting detail is that it punched more ports than you’d expect. It punched the default port that the web interface runs on (8181), a port for an SSL configured web server (5443), and then it also punches ports for 9091, as well as port 8800, which I’m not sure what the purpose is. My guess is that these ports were being used by a Terramaster developer, and they didn’t bother to remove the config to punch them before releasing the software.
Some suggested I just disable uPnP on my router, but I personally believe this kind of misses the point. I am a software engineer who regularly dabbles in infrastructure, and therefore could reasonably be expected to figure out how to disable uPnP. Thinking about the average consumer, who wouldn’t have any idea what port forwarding or uPnP is, I’m not so sure they could. Disabling uPnP definitely closes this particular security hole, but the vast majority of consumer routers are going to have this feature on, and therefore the vast majority of these NAS products in the wild are likely exposing themselves unwittingly. I am hoping that Terramaster will fix this issue in their product, and therefore unwitting users who aren’t aware of what uPnP is suddenly find themselves more secure, assuming they update!
Others suggest buying a new router which would support having two separate LAN networks so that this gear could be put on a LAN that is denied direct access to the internet/not have uPnP. This again I don’t see regular consumers doing en masse. I could do it, and very well may in the future, but I don’t really feel the need to upgrade my networking gear currently. It works, and I am happy with it.
This is why I went spelunking into the device itself. Thankfully Terramaster provides root on these boxes, which is nice of them. This led me to discover the fix I did.
Either way, one detail I got the most comments about was whether disabling uPnP was really a hit to convenience. Somebody emailed me questioning this specifically, as well as pointing out that GRC has a check to make sure your router isn’t allowing services on the internet to punch open ports on your router to hosts behind it. I had no idea this was a problem, and facepalmed pretty hard that this ever was, but nevertheless I replied:
If I’m being totally honest with you, this was more of a ‘feeling’ than it was an analytical decision. I should have known better than to assume I’d get away with that in a blog post like this, but I wasn’t quite expecting it to blow up the way it did!
I am reasonably confident in my router (author sidenote: lol), it’s actually not the trashiest ISP provisioned router I’ve ever had and the GRC uPnP exposure check is not flagging anything up.
I am strongly considering writing a blog post in future addressing this though - essentially my plan is to disable uPnP without making any other changes and seeing what breaks, if anything. It is completely possible I am very wrong that this is necessary these days. I am already port forwarding certain stuff I need externally accessible, but I’d be curious if the various consumer level stuff I’ve got floating around manages to keep working.
Thanks for contacting me!
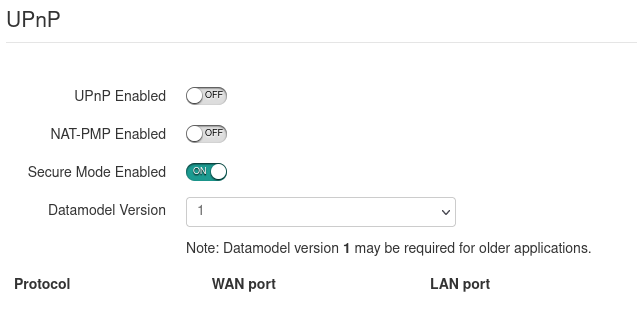
So here I am, money where my mouth is. I’ve disabled uPnP and NAT-PMP on my router entirely.
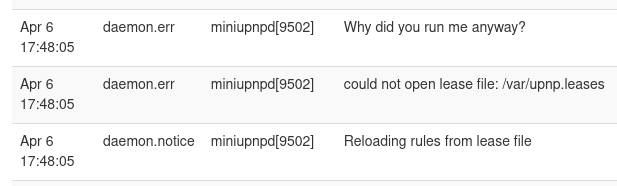
Turning uPnP off led to some rather amusing error messages in my routers debug log
I’ll come back to this in a months time and see whether there has really been a hit to ‘convenience’ or whether I was truly wrong on this. I’m always happy to learn!
Let me know what you thought! Hit me up on Mastodon at @kn100@fosstodon.org.